Intelligent Device-Based ATO Prevention Built for Modern Mobile Apps
Evaluates every session with AI-powered scoring and behavioral analytics, allowing you to protect users without slowing them down.
See how it works300+
Countries and regions with detected devices.
1 BILLION+
Distinct Browser and mobile devices detected
357K
Real time device intelligence processes daily API event


Great business come with Great protection.
Most of them agreed with it. Now see below, who else do you recognize?


Account Takeover: Silent, Costly, and Rapidly Expanding
Attackers use credential theft, SIM swapping, and remote access tools to impersonate users, often without detection.
Sensitive User Data
In apps with digital wallets, attackers could steal funds stored in the user's wallet, leading to direct financial loss for both the user and the business.
Digital Wallet Balances
In apps with digital wallets, attackers could steal funds stored in the user's wallet, leading to direct financial loss for both the user and the business.
App Reputation and User Trust
If users experience account takeovers, they may lose trust in the app, resulting in negative reviews, uninstalls, and a damaged reputation that's difficult to rebuild.
Customer Retention and Lifetime Value
Once users are affected by security breaches, they are likely to stop using the app, decreasing long-term customer loyalty and reducing potential future revenue.
Compliance with Financial and Privacy Regulations
A breach could also result in a failure to meet legal requirements, exposing the company to fines, lawsuits, and regulatory scrutiny.
Brand Loyalty
A loss of brand loyalty often leads to decreased market share, as users may turn to competitors with better security measures.
How Keypaz Stops Account Takeover Before It Happens
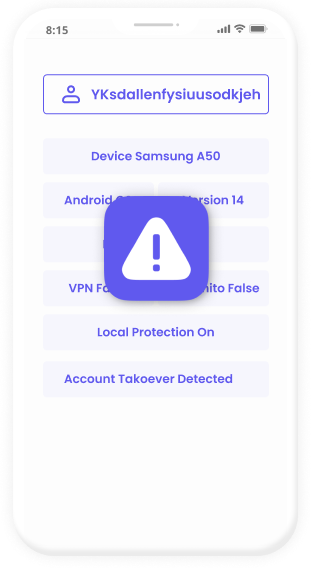
Device Insight
Keypaz doesn't just identify the device—our system analyzes its behavior. By understanding how the device interacts with your app, Keypaz assesses whether it can be trusted. If the device shows suspicious behavior, access is blocked before login.
Behavioral Analysis
Keypaz continuously monitors user behavior, such as typing speed, gesture flow, and screen navigation. If any anomalies are detected—like inconsistent patterns—it signals potential fraud, such as bot activity or session hijacking, stopping it before it becomes an issue.
SIM & Network Monitoring
We track SIM card changes, network carrier mismatches, and IP anomalies in real-time. Suspicious activities, like SIM swapping or VPN masking, are immediately flagged and blocked to prevent attackers from gaining unauthorized access.
Advanced Environment Detection
Keypaz detects compromised environments, such as rooted or jailbroken devices, emulators, or cloned app instances.
Protect Your Users from Account Takeover—Starting Today
Discover how Keypaz helps you detect and block high-risk sessions before login even happens.
Request a Demo



